DDoS Mitigation for DIA
Get Dedicated Internet Access with automated, 24/7 DDoS protection
What is a distributed denial-of-service (DDoS) attack?
A distributed denial-of-service (DDoS) attack is a type of cyber threat that aims to disrupt websites, applications or online services by overwhelming them with excessive internet traffic.
Unlike a traditional denial-of-service (DoS) attack, which typically comes from a single source, a DDoS attack is “distributed” – launched simultaneously from multiple systems or IP addresses. This makes it much harder to trace and defend against.
DDoS attacks are often used to:
- Disrupt business operations
- Demand ransom payments
- Make political or ideological statements
While they don’t breach systems or steal data, they can cause serious downtime, damage customer trust and lead to financial losses.
How do DDoS attacks work?
A DDoS attack works by overwhelming a website, server or network with an extraordinarily high volume of traffic from multiple sources, causing it to slow down or crash.
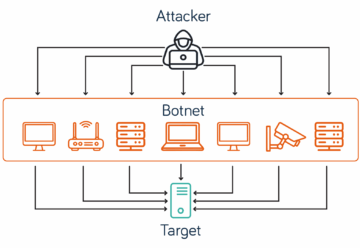
These attacks are typically launched using a network of compromised devices connected to the internet. Computers, servers or Internet of Things (IoT) devices are infected with malware, turning them into “bots” under the attacker’s control. Together, these bots form a “botnet”.
The botnet then sends a flood of requests to the target’s IP address – all at once from many different locations. This sudden surge overwhelms the system’s capacity, denying access to genuine users and effectively taking the service offline.
DDoS attack
Types of DDoS attacks
DDoS attacks can be categorised into three main types, targeting various aspects of a network or service. They typically focus on specific layers of the OSI model, particularly the Network Layer (layer 3), the Transport Layer (4) and the Application Layer (7).
Volumetric attacks
Volumetric attacks aim to saturate the target's bandwidth by overwhelming it with a massive volume of traffic. Techniques include UDP floods, DNS amplification and ICMP floods. These attacks typically operate at layers 3 and 4 of the OSI model.
Protocol attacks
These attacks exploit weaknesses in network protocols to exhaust server resources. Examples include SYN floods, Ping of Death and IP fragmentation attacks. They also target layers 3 and 4, disrupting how systems handle connections.
Application-layer attacks
Targeting layer 7, application-layer attacks mimic legitimate user behaviour to overwhelm specific applications or services. Common methods include HTTP floods and Slowloris attacks, which can be difficult to detect as they look like normal traffic.
Whatever the method, the impact of a DDoS onslaught can be severe, taking critical services offline and damaging customer trust.
The impact of DDoS attacks on UK businesses
UK businesses faced a 550% year-on-year surge in web DDoS attacks in 2024, according to the Radware 2025 Cyber Threat Report. The sharp increase was largely driven by hacktivist activity and rising geopolitical tensions.
The consequences have been significant. Across sectors, DDoS incidents have caused operational disruption, financial loss and reputational harm.
For example, a DDoS attack on the Royal Mail in 2024 caused widespread parcel delivery delays. Meanwhile, the telecommunications sector was the target of 43% of global network DDoS attacks, followed by the financial sector at 30%.
The lesson is clear: whatever your industry or business size, DDoS protection is now essential.
How to mitigate DDoS attacks effectively
DDoS mitigation starts by monitoring traffic to establish normal traffic patterns. That way, anomalies like bot activity or spoofed requests can be identified in real time.
Traffic is then filtered using IP reputation checks, deep packet inspection and rate limiting. The best systems use scrubbing, which removes malicious traffic before it reaches your network. In contrast, blackholing – which drops all traffic to a target IP address – can block both malicious and legitimate traffic.
Manual mitigation is no longer viable as modern attacks are too large and fast for human response alone. Instead, you need a DDoS protection service with:
- Real-time monitoring: Detects abnormal spikes or suspicious patterns before they disrupt services
- Layered defence: Protects at the network, transport and application layers to guard against all attack types
- Traffic filtering and rate limiting: Controls the flow of requests to prevent overload
- Scalable infrastructure: Includes built-in capacity to absorb attacks while mitigation takes effect
- Always-on protection: Automated tools ensure round-the-clock defence, even when you're not watching
This is how we’ve designed our future-ready DDoS protection for Dedicated Internet Access (DIA) – to keep your services secure and connected at all times.
Neos Networks DDoS protection for DIA
Our DIA service now offers three levels of DDoS protection, so you can choose the option that fits your business needs:
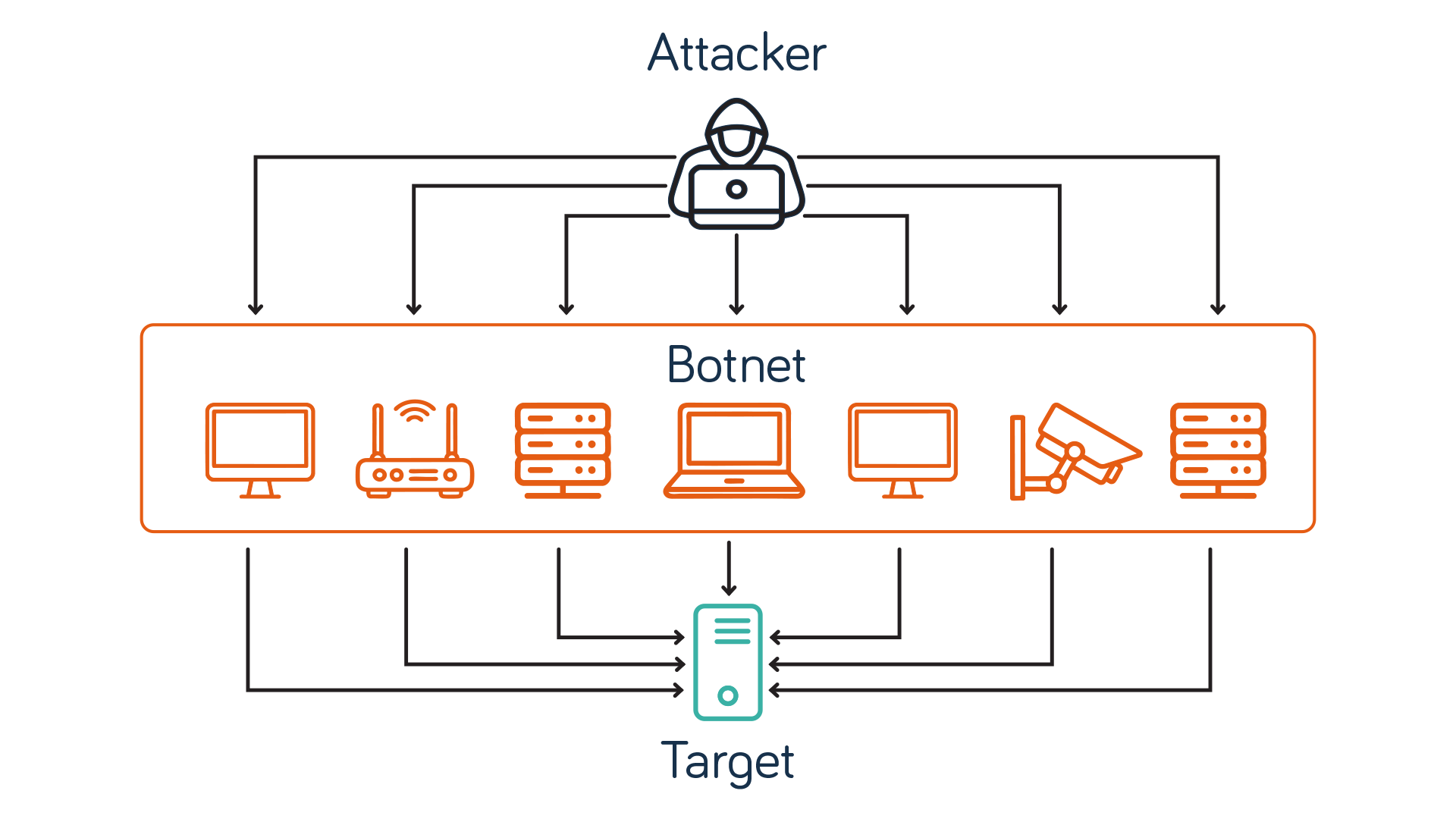
1. DDoS Mitigation – Always-on, circuit-level protection
- Real-time auto-mitigation of volumetric, protocol and application-layer attacks
- 24/7 monitoring of all IPv4 and IPv6 traffic
- Weekly DDoS threat reports
- Easy customisation to fit your business needs
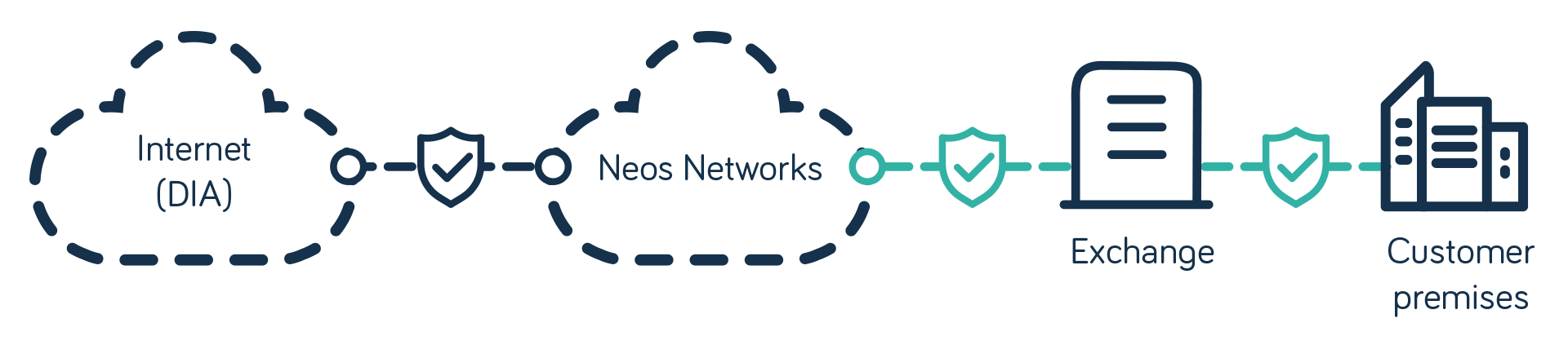
2. DDoS Monitoring – Visibility with upgrade path
- Continuous DDoS monitoring for each DIA circuit
- Monthly DDoS threat reports
- Fast upgrade to DDoS Mitigation when needed
3. DDoS Standard – Core protection included as standard

- DDoS-protected core network (tails not included)
- Included with all DIA circuits at no extra cost
Protect your business against tomorrow’s threats today. Get a quote for DIA with DDoS protection in minutes using LIVEQUOTE.